Manual provisioning in unified communications (UC) can lead to many security risks – both accidental and in some cases, malicious. In this article, we cover the biggest risks and how an automated provisioning solution can help solve them.
When you think about your company’s UC provisioning processes, do you think about security?
If you’re like most companies, there is probably room for improvement when it comes to the security of your provisioning process. This is especially true if your process is filled with manual tasks because these tasks could be implemented incorrectly, and thus exposing your company to substantial risks.
Let’s discuss the biggest ones.
3 Big Risks of Manual UC Provisioning
There are three main risks related to manual provisioning. Each one of them could result in service disruptions or outages of critical UC applications.
#1. Improper Access
If you’re still working with a manual provisioning process, you might be forced to give your administrators too much access to critical functions in your UC applications.
On the surface, this may not seem like a big deal. However, that access can lead to a wide range of consequences from accidental service disruptions to malicious misuse.
Ideally, people should be working in a provisioning solution rather than directly in the UC applications, and you only want to give access to the functions that people need, without giving them the keys to the city.
#2. Human Error
A manual user provisioning process introduces many opportunities where human error can enter the equation. And the more manual steps in your process, the greater the chance for more errors to occur.
Manual provisioning work is repetitive, and people tend to get bored of repetitive work. They rush to get it done, and they make mistakes.
Errors may not seem like that big of a security risk, but one mistake can bring down your UC applications for hours – grinding your company’s communication and productivity to a halt.
#3. Malicious Activity
Malicious activity regarding your provisioning process is less common, but the results are just as detrimental.
Like any security vulnerability, your provisioning process can leave the door open for malicious actors. It can also make intentional misuse by your employees possible.
While UC applications are not traditionally a prized target for hackers, companies should do their due diligence in all aspects of cybersecurity. That includes their UC environment.
4 Automated Features That Make UC Provisioning More Secure
Now that we’ve gone through the risks associated with manual provisioning, let’s get into what you can do about them.
The short answer to mitigating the security risks associated with manual provisioning is upgrading to an automated UC provisioning solution packed with features that lock down your provisioning process.
Here are the most important features to look out for.
#1. Templated Jobs
The first thing needed to mitigate risk is a way to eliminate human error from the provisioning equation. That’s where pre-configured MACD templates come in.
Job templates make executing common MACD jobs easier for the UC administrator. They ensure common provisioning jobs and account set-ups are consistent and mistake-free every time. That makes your provisioning process more secure. On top of that, templates make your process more efficient and easier to do in less time.
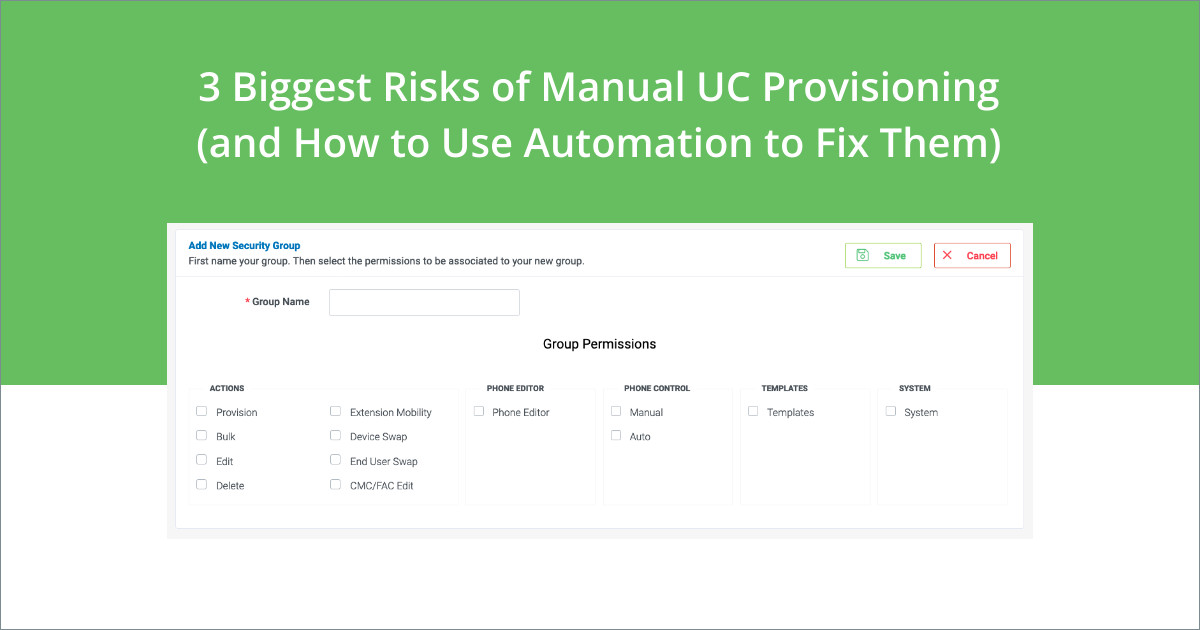
#2. Role-Based Access
Role-based access allows you the option to designate who gets access to what features and functions. That means you can limit what your administrators can see and manipulate.
It can also help you save significant engineering time. The combination of role-based access and templated jobs allows you to securely offload provisioning work to a HelpDesk, so your UC engineers can focus on more strategic, higher-impact projects.
#3. End User Self-Service Portal
Another useful feature that improves security is an end user self-service portal. This portal allows your employees to make changes without having to contact a UC administrator or put in a HelpDesk ticket.
So, they can make simple changes to their profiles and application settings without the risk of braking anything critical. You can allow end users to update basic settings such as their voicemail PIN, call forwarding settings and much more.
#4. Audit trails
Extensive audit trail tracking and reporting is an essential part of UC security. It’s important to know when changes were made and who made them. This allows your UC engineering team to track changes and keep a running record of how people are provisioning UC applications. It is also a great tool to identify training needs.
Conclusion – Automated Provisioning Ensures Secure Provisioning
If you’re not looking into the security of your provisioning process, it’s only a matter of time before your risk exposure catches up to you. Replacing your manual tasks with an automated provisioning solution will mitigate those risks and help you avoid a completely preventable security threat from sidelining business operations.
Looking to lock down your provisioning processes? Talk to an expert at Akkadian Labs today. Let us show you how our automated provisioning solution can solve security.